Remote access scams are social engineering attacks where fraudsters convince users to install or open remote desktop tools like TeamViewer or AnyDesk. Once inside, they hijack login flows, harvest credentials, and often bypass MFA, opening a hidden path to account takeover (ATO). These scams are rising fast, exploiting customer trust and evading traditional fraud controls.
Security teams may rely on trusted device signals, MFA success, and login hygiene to flag risk, but remote access scams exploit all three. These scams hijack the user’s own device and session, turning legitimate logins into attack vectors.
What Are Remote Access Scams?
Remote access scams are a type of tech-support or impersonation fraud in which criminals convince victims to give remote access to their device. Once connected, attackers can observe or manipulate browser activity, intercept login credentials, and trick users into handing over MFA codes, often leading to silent account takeover.
Because attackers operate within the user’s legitimate session, traditional controls often fail to detect anything unusual.
Remote Access Scam Losses: 2023–2025 Trends by Region
- In the United States, total online-crime losses reported to the FBI reached $12.5B in 2023 and $16.6B in 2024, a 33% increase year-over-year, according to the FBI’s Internet Crime Report. Tech-support and customer impersonation scams were cited as key vectors – many involving remote access tools.
- In Australia, combined scam losses reached A$2.03B in 2024, down 25.9% from 2023. Remote access scams accounted for A$106M of that total, according to the Australian government’s Targeting Scams Report 2024.
- In the UK, the finance sector reported £1.17B lost to fraud in 2023, according to UK Finance. Impersonation scams frequently include a request for remote access during the social-engineering flow.
These aren’t fringe cases. They’re multi-billion-dollar blind spots of increasingly common and growing remote access threats for which many businesses lack scalable responses.
How Remote Access Scams Work
Attackers use a combination of social engineering and remote access tools. A typical anatomy looks like this:
- Initial contact, often as bank or tech support. Common pretexts include account compromise alerts, refund errors, or urgent identity verification requests.
- Tooling step where the victim is steered to install or open a remote app, or to accept a browser-based sharing session.
- Guided actions such as logging in, sharing one-time codes, or moving funds under the guise of “securing” the account.
- Cleanup to reduce traces, including closing sessions and urging the victim to stay silent “for security.”
This is sequence is common in modern-day account takeover fraud and how it unfolds, where attackers operate upstream of authentication and inside the Window of Exposure (WoE), before traditional controls engage.
Tool-Specific Scam Variants
Security teams often search for guidance tied to tools like TeamViewer scam prevention, AnyDesk scam protection, and LogMeIn scam detection. These terms matter because buyers often look for security guidance mapped to the tools criminals co-opt.
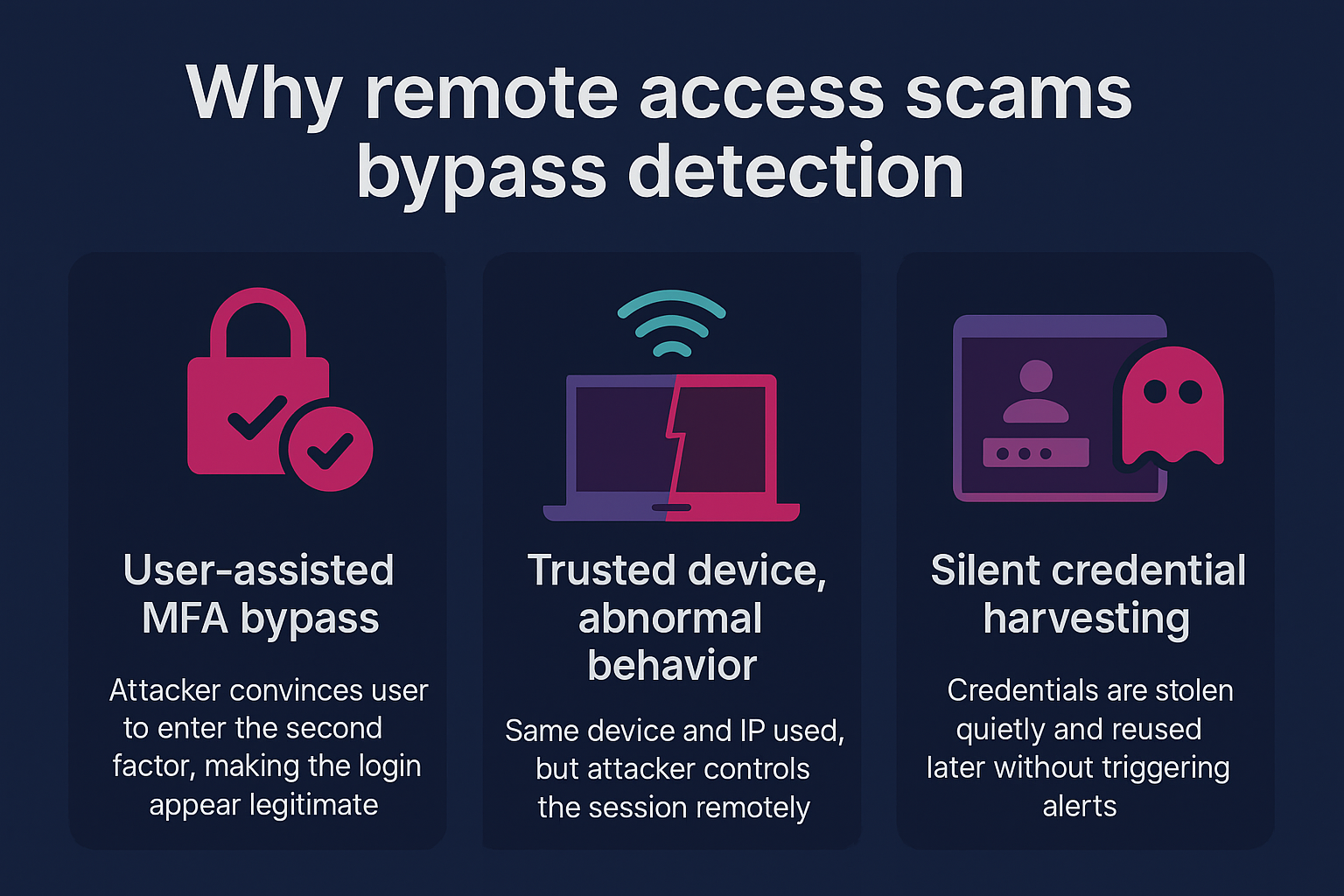
Why Remote Access Scams Bypass Traditional Detection Methods
Many teams depend on perimeter checks and basic behavioral signals. Remote access scams sidestep them in three ways:
- User-assisted bypass of MFA. The victim supplies the second factor, so the login appears legitimate.
- Trusted device signals. Because the attacker controls the victim’s session directly, IP or device fingerprint can look normal while session behavior is off.
- Credential theft with no failed login attempts to trigger alerts. Attackers may harvest credentials for later replay, minimizing failed attempts that would trigger rate-based rules.
Is real-time phishing bypassing your MFA?: How to Detect & Stop Reverse Proxy Phishing Attacks in Real-Time
Why Traditional Detection Fails
These patterns explain why detection must include suspicious login detection, geo-location anomaly detection, and indicators of remote control at the moment of login or credential entry.
Business Impact of Remote Access Scams
Remote access scams create a multi-front problem for enterprises:
- Direct fraud losses and reimbursements, particularly where consumer protection standards expect strong prevention.
- Operational drag on SOC, fraud, and customer support teams due to escalations and disputes.
- Regulatory and reputational exposure when victims report brand impersonation or inadequate warning mechanisms.
How Effective Remote Access Scam Protection Works
Effective remote access scam protection should begin when the remote connection is first established, during session initiation. Key defensive layers typically include:
-
Remote session anomaly detection – Monitoring for behaviors consistent with screen-sharing or remote control attempts.
-
Suspicious login pattern analysis – Correlating device, session context, and prior exposure to phishing to identify high-risk access attempts.
-
Geo-location signals – Surfacing impossible travel or unexpected location changes to flag potential compromise.
-
Adaptive authentication – Requiring additional verification for sessions deemed high-risk before account access or profile changes are allowed.
-
User awareness prompts – Providing clear warnings when activity suggests potential fraud, helping disrupt the scammer’s flow.
Where Memcyco Goes Further
Most solutions stop at anomaly flags or secondary verification. Memcyco adds browser-level visibility and advanced deception techniques to expose and block attackers in real time. This ensures that even if scammers convince a victim to initiate a session, the attack can be detected, disrupted, and contained before account takeover succeeds
Related reading: How Browser-Level Signals Prevent Credential Stuffing
How Does Real-time Remote Access Scam Protection Outperform Legacy Controls?
Legacy security controls focus on post-login anomalies, rate limits, and phishing site detection. But remote-access scams unfold inside the user’s own session, on a trusted device, making them hard to spot.
Real protection means applying a Zero Trust mindset to every session – even those from trusted devices. Just because MFA succeeded or the device looks familiar doesn’t mean the session is safe. Protection must start at login, using session-aware signals to catch remote control, credential replay, and attacker guidance in motion.
How Memcyco Detects and Blocks Remote Access Scams
Memcyco’s preemptive cybersecurity solution provides real-time detection of remote-session signals, suspicious login pattern detection, and geo-location anomaly detection, paired with targeted user warnings and real-time risk signals that enable step-up verification or access blocks for risky attempts. Decoy credential capabilities neutralize exposed user credentials before they are reused. Deployment is agentless, implemented in site code or via WAF, which shortens time to value and avoids client-side friction. These measures lower fraud costs, reduce escalations, and improve digital trust by stopping ATO paths that rely on remote access and social engineering.
Secure Remote Access Best Practices for Fraud and Security Teams
- Instrument the login. Add browser-level checks for remote control signals and correlate with device risk.
- Tune suspicious-login rules for user-assisted MFA bypass patterns, not only failed attempts.
- Deploy in-session warnings that are specific to remote access scams and reference the brand’s official guidance.
- Use decoy credentials to make harvested data unusable and to attribute replay attempts to attack devices.
- Integrate with the fraud engine so high-risk sessions trigger step-up verification before sensitive profile changes.
- Educate support agents to recognize remote-access red flags during calls and to escalate correctly.
Get the Unfair Memcyco Advantage and Stop Remote Access Scams
Remote access scams aren’t going away – they’re getting smarter, faster, and harder to detect. But they’re not invisible. With browser-level detection, real-time signals, and the right intervention points, you can expose them as they unfold.
Contact us to schedule a Memcyco product demo. Find out why global enterprises are replacing outdated defenses with Memcyco’s preemptive cybersecurity solution.
Related reading:
- Disrupting AI-Powered Phishing: What CISOs Must Do Now
- How to Prevent Phishing and ATO From DNS Cache Poisoning in Real Time
- Evil Twin Attack Prevention: Stop Real-Time Phishing to ATO
FAQs About Remote Access Scams
What is a remote access scam?
A social-engineering attack where criminals pose as bank or tech support, convince a user to install or start a remote tool, then guide the victim to log in or move funds under false pretenses. These incidents commonly sit inside tech-support and government-imposter categories in official reporting.
How can I spot a remote access scam quickly?
Unsolicited calls that pressure you to install a remote tool, pop-ups claiming your device is infected, or anyone asking for codes or to watch you log in are red flags. Hang up, go directly to your provider’s website, and contact support through verified channels.
Does MFA stop remote access scams?
MFA helps, but these scams often coerce the user to provide the second factor during a live remote session. Combine MFA with suspicious-login detection, geo-location checks, and in-session warnings to prevent user-assisted bypass.
Which tools do scammers misuse most?
Attackers frequently reference popular tools, then ask victims to install or open them. Buyers often search for TeamViewer scam prevention, AnyDesk scam protection, and LogMeIn scam detection to find guidance that maps to those tool names.
How does Memcyco detect suspicious remote sessions?
By evaluating browser-level indicators, login context, and device signals in real time, Memcyco identifies patterns consistent with remote access or remote control activity. These insights enable targeted warnings, access blocks, or customer-managed step-up verification flows. Decoy credentials neutralize harvested logins before reuse on the genuine site.
What measurable outcomes should teams expect?
Fewer successful ATOs seeded by remote access, lower reimbursement and escalation volumes, and improved customer trust due to visible, timely warnings and safer login flows.



















